TRACERT – trace the route to a given node in the Windows command line. What secrets will the Tracert team help you learn?
If you have ever contacted your Internet provider or technical forums with complaints about unstable connections, you are probably already familiar with the “tracert” command. Support specialists often ask users to run it on the command line and report the result. This helps them determine the source of the problem.
Maybe you were even surprised how an incomprehensible set of characters can help solve network problems? What do these numbers, columns and rows mean? If you want to learn how to use and understand tracert as well as professionals, this article is for you.
Purpose and application of Tracert in practice
T racert- not just some abstract command that the command line understands, but a full-fledged program. More precisely, a service console (without a window interface) Windows application designed to determine the path along which network packets are sent from one node to another. The application name is derived from “trace route”, which means “route tracing”.
The Tracert program is a native component of Windows (installed on the computer along with the OS), its executable file – TRACERT.exe, is permanently located in the %windir%/system32 folder.
To make it easier to understand how the tracer works, let’s imagine a network packet as a regular package that you sent by mail to a neighboring city. On its way to the addressee (final node), the package makes several stops at sorting points (intermediate nodes), where it is registered and sent further. You, as the sender, knowing the postal track number of the parcel, can monitor its movement on special websites. If the shipment is not delivered on time, you will easily find out at what stage of the journey it was lost.
Tracert works in a similar way. Only it provides information about not postal, but online shipments.
Notice the similarities between these entries:

Tracing is used as one of the tools for comprehensive diagnosis of network failures. So, with its help you can determine:
- At what level does the blocking of an inaccessible web resource occur: at the home network level (packets are not sent beyond the gateway), within the provider’s network or outside it.
- Where packets go astray from the correct route. For example, the reason that instead of the requested message may be a malicious program on the user’s computer or a redirection from some network node.
- Is the web resource what it claims to be?
How tracing works
As you know, the application is launched and executed in the Windows command line. Most often it is used without additional parameters. The command to trace the route to the desired web resource looks like this:tracertsite_url or IP_site. For example, tracert Mts.ru,tracert 91.216.147.50
The answer will be something like this:

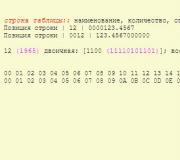
Below I will explain what these numbers and entries mean, but first, to make it clear, let’s look at the principle of operation of the tracer.
Once you enter the above instruction in the command line and press Enter, the application will send a series of three ICMP packets to the specified web resource. One of the service fields of each packet indicates the TTL value - the number of permissible transmissions between network nodes or, as they say, the “lifetime” of the request. When a shipment moves from router to router, the TTL value decreases by one. When it reaches zero, forwarding stops, the packet is discarded, and the sending computer receives an ICMP notification about it.
The TTL value of the first batch of ICMP requests is 1. The first node to which it arrives will subtract one from this value. Since the “lifetime” of the packets becomes zero, they will be thrown “to the dustbin of history”, and the sender will receive a response “letter” indicating the name and IP address of this node.
The TTL value of the second batch will be equal to two (the response will be received from the second node), the third – three, etc. Sending with the TTL increasing by 1 will continue until the data is received by the recipient.
How to read the trace result

The second, third and fourth columns contain RTT values - the time elapsed from the moment the request was sent until the response was received (as you remember, the batch consists of three packets). The smaller it is, the faster the transfer occurs. If it is more than 4 seconds, the timeout interval is considered exceeded.
The last column is the names and addresses of the intermediate and final nodes.
Asterisks instead of values do not always indicate the unavailability or malfunction of a network device (as some sources say). Most often, this is simply a setting that does not allow ICMP response messages to be sent (measures to protect a website from DDoS attacks). If your request reaches the endpoint safely in a reasonable time, there is nothing to worry about.
The reason for the failure of delivery of ICMP packets (if the request never reaches the recipient) may be the inoperability (disconnection or malfunction) of the network device or the security policy (this action is blocked by the network administrator).
Tracert parameters
If you run the tracert command without specifying a web resource, the console will display help information about the launch parameters or, as they are called, application keys.
The keys are written separated by a space after the command before the name of the website if you need to change something in the standard settings. For example:
Tracert –w 1000yandex.ru, which means: trace the route to yandex.ru with a response timeout of 1000 ms.
Below is a list of parameters with their meanings.
You see, everything turned out to be simpler than it seemed. By the way, there are still a lot of such useful gizmos in the bins of Windows. I’ll definitely tell you about them next time too. I hope it will be useful.
Also on the site:
What secrets will the Tracert team help you learn? updated: December 5, 2016 by: Johnny Mnemonic
You cannot “go” online to a certain site or group of sites, or even an entire segment of the Internet has suddenly become inaccessible to you. One of the tools for “fixing the Internet” is route tracing. What is it?
The Internet is so integrated into all areas of modern life, including business and professional life, that connection problems can cause significant financial losses.
Of course, any Internet service provider (service provider for using the World Wide Web) provides technical support services. Only now the technical support workers are “eager” to answer a call in much the same way as a mechanic from the housing office: it’s good if you wait until the evening. And if problems overtook you on weekends or holidays... That’s why you often have to take the situation into your own hands. Carrying out, if not repairs, then diagnosing an Internet connection is the same necessary skill of a modern person as the ability to fix a faucet or at least turn off the water until the emergency team arrives.
One of the tools for “fixing the Internet” is route tracing. What is it?
Suppose you cannot “access” a certain site or group of sites online, or even an entire segment of the Internet has suddenly become inaccessible to you. What could cause this to happen? As mentioned above, the modern worldwide network is a very complex system. If you “access”, for example, Odnoklassniki, this does not mean that your computer connects directly to the site’s server. Information, before ending up on your computer, passes through a number of so-called nodes. Moreover, for different sites and different users this path (route or route from the English route) will also be different. Tracing allows you to “ring” the entire path, identifying the problem node.
How to make a trace?
To do this, you will need the traceroute utility. The principle of its operation is simple: the program sends an information signal - a data packet - in the problematic direction, receiving a response from each of the nodes - a kind of information echo. Thus, you can measure the time it takes for a signal to travel from one node to another, easily identifying the “weak link”.
There is no need to rush to look for where to download such a useful thing: the traceroute utility is already built into your operating system.  To run it, use the tracert command. So what you need to do:
To run it, use the tracert command. So what you need to do:
- Call the command line. To do this:
- Press the start button on the screen or the win key on the keyboard (the win key on a standard keyboard is located between Alt and Control, it depicts the world-famous logo of everyone’s favorite Windows operating system);
- In the menu that appears (start menu), select “Run”. The “run” command allows you to use Windows system utilities that are hidden away from the hands of curious users, since inept use of some programs can harm the operation of the operating system and data stored on the computer. A kind of “foolproofing”. But we are certainly not fools, so we continue;
- In the line that appears after selecting “execute”, enter cmd manually in Latin font and click Ok. The command line is called.
Help: you can quickly call up the “run” line by pressing the win+r combination on the keyboard. Then you can enter cmd.
- Enter the command into the command line tracert name orSite IP(there were problems connecting to it). For example, tracertru.
- We are waiting for the result. As a result, we will see several lines (up to 30), each of which is a node through which information passes. The line will contain the name or IP of the node and the signal transit time in milliseconds (ms – thousandth of a second).
The above described is relevant for the Windows operating system, but how is route tracing performed under Linux? In general terms, it’s similar, only the terminal (analogous to the command line) is called instead of cmd by pressing the key combination Ctrl+Alt+t, and instead of tracert we enter traceroute. It is also worth noting that tracing in Linux will continue until the user interrupts it himself by pressing ctrl+c.
What will the result give us? The longer the packet takes, the more the site slows down, so we will identify the node responsible for the slowdowns. An impassable node will be indicated by the inscription “Route waiting interval exceeded.” The higher the problematic line in the list, the more local the problem. “Impossibility” at the bottom of the list indicates problems with the site or domain, and at the top - with your provider or in the local network.
Utility for tracing a route to a given node TRACERT.EXE is one of the most commonly used network diagnostic tools. Its main purpose is to obtain a chain of nodes through which an IP packet passes, addressed to an end node whose name or IP address is specified by a command line parameter.
Command line format:
tracert [-d] [-h maxNumber] [-j Node list] [-w timeout] [-R] [-S Source address] [-4] [-6] finalName
Command line options:
-d- do not use resolution in host names.
-h maxNumber- the maximum number of hops when searching for a node.
-j listNodes- free choice of route from a list of nodes (IPv4 only).
-w timeout- timeout of each response in milliseconds.
-R- path tracing (IPv6 only).
-S source address- use the specified source address (IPv6 only).
-4 - forced use of IPv4.
-6 - forced use of IPv6.
The tracing is based on a method for analyzing responses when sequentially sending ICMP packets to a specified address with the TTL field increasing by 1. (“Time of Life” - Time To Live). In fact, this field has nothing to do with time, but is a counter of the number of possible transitions during the transmission of a routed packet. Each router, upon receiving a packet, subtracts one from this field stored in the packet header and checks the resulting TTL counter value. If the value becomes zero, the packet is discarded and an ICMP time-to-live message ("Time Exceeded" message, value 0x11 in the ICMP header) is sent to the sender.
If it were not for the inclusion of the TTL field in IP packets, then in case of errors in the routes, a situation could arise where the packet would forever circulate in the network, forwarded by routers in a circle.
When executing the tracert.exe command, it first sends an ICMP packet with the TTL field in the header equal to 1
and the first router in the chain (usually the main gateway from the network connection settings), subtracting one from the TTL, receives its zero value and reports that the lifetime has been exceeded. Thus, the TRACERT.EXE utility obtains the IP address of the first router involved in delivering packets to the end node. This sequence is repeated three times, so the result line generated by tracert.exe displays three response times after the transition number:
1 1 ms 1 - transition number (1 - first router)
1 ms 192.168.1.1 - its address (or name)
Then the procedure is repeated, but the TTL is set to 2 - the first router will reduce it to 1 and send it to the next one in the chain, which, after subtracting 1, will reset the TTL and report that the lifetime has been exceeded. The TRACERT.EXE utility will obtain the second IP address of the node involved in delivering the packet to the recipient and its response time. The tracing process will continue until the end node whose name or address is specified as a command line parameter is reached, e.g. tracert yandex.ru, or until a fault is detected that prevents the package from being delivered. By default, the TRACERT.EXE utility uses a maximum hop count of 30, which should be enough to reach any node on the planet. If necessary, a different counter value can be set using the parameter -h
Example of execution results tracert google.com
tracert google.com- route tracing to the google.com node
Result:
Trace the route to google.com with a maximum number of hops of 30:
1 1 ms 2 498 ms 444 ms 302 ms ppp83-237-220-1.pppoe.mtu-net.ru
3 * * * .
4 282 ms * * a197-crs-1-be1-53.msk.stream-internet.net
5 518 ms 344 ms 382 ms ss-crs-1-be5.msk.stream-internet.net
6 462 ms 440 ms 335 ms m9-cr01-po3.msk.stream-internet.net
7 323 ms 389 ms 339 ms bor-cr01-po4.spb.stream-internet.net
8 475 ms 302 ms 420 ms anc-cr01-po3.ff.stream-internet.net
9 334 ms 408 ms 348 ms 74.125.50.57
10 451 ms 368 ms 524 ms 209.85.255.178
11 329 ms 542 ms 451 ms 209.85.250.140
12 616 ms 480 ms 645 ms 209.85.248.81
13 656 ms 549 ms 422 ms 216.239.43.192
14 378 ms 560 ms 534 ms 216.239.43.113
15 511 ms 566 ms 546 ms 209.85.251.9
16 543 ms 682 ms 523 ms 72.14.232.213
17 468 ms 557 ms 486 ms 209.85.253.141
18 593 ms 589 ms 575 ms yx-in-f100.google.com
Tracing is complete.
Trace results may contain lines where an asterisk is displayed instead of the node address (node number 3 in the example). This is not necessarily a sign of a faulty router, and most often indicates that the settings of this node prohibit the sending of ICMP messages for security reasons and to reduce the load on the channel in the event of certain types of DDoS attacks. For example, similar settings are used in Microsoft networks. The corporation's servers do not respond to ping and do not allow tracing the route to them.
Examples of using TRACERT
tracert google.com- trace the route to the node google.com.
tracert 8.8.8.8- trace the route to a node with an IP address 8.8.8.8
tracert -d yandex.ru- trace the route to the node yandex.ru without resolving IP addresses into hostnames. Tracing in this mode is faster.
tracert -d -6 ipv6.google.com- perform tracing using the IPv6 protocol.
Example of trace results using IPv6 protocol:
trace to ipv6.google.com (2a00:1450:4013:c00::71), 30 hops max, 40 byte packets 1 2a02:348:82::1 (2a02:348:82::1) 8.087 ms 8.063 ms 8.086 ms 2 te0-22.cr1.nkf.as49685.net (2001:4cb8:40b:1::1d01) 2.143 ms 2.129 ms 2.103 ms 3 amsix-router.google.com (2001:7f8:1::a501: 5169:1) 1.379 ms 1.415 ms 1.422 ms 4 (2001:4860::1:0:87ab) 1.437 ms (2001:4860::1:0:87aa) 2.157 ms (2001:4860::1:0:87ab ) 1.408 ms 5 (2001:4860::8:0:87b0) 1.494 ms 1.469 ms (2001:4860::8:0:87b2) 8.350 ms 6 (2001:4860::8:0:b1b7) 5.364 ms 5.321 ms 4.748 ms 7 (2001:4860::2:0:8651) 4.653 ms 6.994 ms (2001:4860::2:0:8652) 13.926 ms 8 ee-in-x71.1e100.net (2a00:1450:4013 :c00::71) 4.732 ms 4.733 ms 4.783 ms
2) What is the principle of relative addressing? In what situations does it appear?
3) Cell D7 contains the formula (C3+C5)/D6. How does it change when you move this formula to a cell:
a) D8; b) E7; c) C6; d) F10.
2.What parts does a file name consist of?
3.Who or what names the file?
4.Who or what assigns a file extension?
5.How many characters can a file name include?
6.How many characters are usually allocated for a file extension?
7.What needs to be done with the disk so that files can be stored on it?
8.What areas is the disk divided into when formatting?
9.In what case is the file system single-level?
10.How to write down the path to a file?
11.What kind of software does the operating system belong to?
12. What information should the operating system have to organize access to files?
13.Where is the currently running program and processed data stored?
14.What is a catalog called?
15.When does the operating system boot?
16.What is an operating system?
17.What is the name of a logical drive?
18.Which directory is called the root?
19.What is the state of the operating system called when it stops producing results and responding to requests?
20.What happens to OS files during the boot process?
21. The user, moving from one directory to another, sequentially visited the directories LESSONS, CLASS, SCHOOL, D:\, MYDOC, LETTERS. With each move, the user either went down to a lower level in the directory, or went up to a higher level. What is the full name of the directory from which the user started moving?
1) D:\MYDOC\LETTERS
2) D:\SCHOOL\CLASS\LESSONS
3) D:\LESSONS\CLASS\SCHOOL
22. Determine which of the specified file names does not satisfy the mask: ?*di.t?*
4) melodi.theme
23.The file Literature_List.txt is stored in a certain directory. In this directory, we created a subdirectory named 10_CLASS and moved the file List_literature.txt into it. After which the full file name became D:\SCHOOL\PHYSICS\10_CLASS\Literature_list.txt.
What is the full name of the directory where the file was stored before it was moved?
1) D:\SCHOOL\PHYSICS\10_CLASS
2) D:\SCHOOL\PHYSICS
24. Which of the files matches the mask??P*.A??:
1)What is information?2) What actions can we perform with information?
3)How and where can we store information?
4) What types of storage media exist?
5)How can we transfer information?
6)What is a code?
7)What is coding?
8) Encode the word: Ivanov Ivan.
9) How else do you think information can be encoded?
10)What is hardware?
11)What is software?
12) What is a processor, why is it needed?
13) Why are fans needed in a computer?
14) What do you need a printer, scanner, mouse, keyboard and speakers for?
2.What is graphic? Do raster graphics files store color information for each pixel of an image on screen primitives?3.What information is stored in raster files and vector files?
4.What is a graphic coordinate system?
5. What means (software, technical) are used to obtain raster and vector graphic information?
6. Which method of presenting graphic information is more economical in terms of memory use?
7.Why is raster files compressed?
8. How do raster and vector images react to resizing and rotation?
Get the raster code and vector description to display the letters "N", "L", "T" on a black and white screen with an 8x8 graphic grid.