Standard windows ports. "ports and what they are responsible for" "what are the ports and what are they for" "communication protocols on the Internet" "manual"
A port in computer networks is a communication endpoint in an OS. The term is also used for hardware devices, but in software it refers to a logical construct that identifies a particular type of service or process. The port is always associated with the host's IP address or communication protocol type. It completes the session address assignment. A port is identified for each protocol and address by a 16-bit number, also known as the port number. Often specific port numbers are used to define specific services. Of the several thousand listed, 1024 known numbers are protected under a special agreement. They define specific types of services on a host. Protocols that primarily use ports are used to control processes. An example is the TCP transmission control protocol or the User Datagram Protocol of the Internet protocol suite.
Meaning
TCP ports are not needed on direct point-to-point links when computers at each end can only run one program at a time. The need for them arose after these machines were able to execute more than one program at the same time. They were connected to modern packet-switched networks. In the client-server architecture model, ports, applications, and network clients are connected to service initiation. They provide multiplexing services after the initial exchange of information is associated with a port number. It is freed by switching each request service instance to a leased line. Connected to a specific number. Thanks to this, additional customers can be served without any waiting.
Details
The UDP and TCP data transfer protocols are used to indicate the destination port number and source in their segment headers. The port number is an unsigned 16-bit number. It can range from 0 to 65535. TCP ports, however, cannot use the number 0. For UDP, the source port is optional. A value equal to zero means its absence. This process binds input or output channels using a transport protocol, port number, and IP address over an internet socket. This process is also known as bonding. It enables the reception and transmission of information over the network. The operating system network software is used to transmit outgoing data from all application ports to the network. It also forwards incoming network packets by matching the number and IP address. Only one process can bind to a given IP address and port combination using the same transport protocol. Application crashes, also known as conflicts, occur when multiple programs try to communicate with the same port numbers on the same IP address using the same protocol at the same time.
How they apply
It is quite common for applications that implement shared services to use a specially reserved and well-known list of UDP and TCP ports to accept client service requests. This process is also known as listening. It involves receiving a request from a well-known port and establishing a conversation between the client and server one to the other using the same local port number. Other clients may continue to connect. This is possible because a TCP connection is identified as a chain that consists of local and remote ports and addresses. Standard UDP and TCP ports may be defined by convention under the control of the IANA or the Internet Assigned Numbers Authority. As a rule, the core network services, primarily the World Wide Web, use small port numbers, less than 1024. In many operating systems, applications require special privileges to bind to them. For this reason, they are often considered critical to the operation of IP networks. The end client of a connection, on the other hand, tends to use more of them, allocated for short-term use. For this reason, there are so-called ephemeral ports.
Structure
TCP ports are encoded in the packet header of the transport packet. They can be easily interpreted not only by receiving and transmitting PCs, but also by other components of the network infrastructure. Firewalls in particular are typically configured to distinguish between packets based on their destination port numbers and their source. A classic example of this is redirection. Attempts to connect in series to a range of ports on the same computer are also known as scans. Such procedures are usually associated either with malicious failure attempts, or with the fact that network administrators are specifically looking for possible vulnerabilities in order to prevent such attacks. Actions aimed at opening a TCP port are recorded and controlled by computers. This technique uses a number of spare connections in order to ensure uninterrupted communication with the server.
Examples of using
A prime example where UDP and TCP ports are heavily used is the Internet mail system. The server is used to work with e-mail. In general, he needs two services. The first service is used for transport by e-mail and from other servers. This is achieved using the Simple Mail Transfer Protocol (SMTP). The SMTP service application typically listens on TCP port number 25 in order to process incoming requests. The other service is POP or IMAP. They are required for email client applications on users' machines in order to receive email messages from the server. POP services listen on TCP port 110. All of the above services can run on the same host machine. The port number, when this occurs, distinguishes the service requested by the remote device. If the server's listening port number is defined correctly, this parameter for the client is determined from the dynamic range. Clients and the server individually, in some cases, use certain TCP ports that are assigned by IANA. DHCP is a good example. Here, the client uses UDP 68 anyway, and the server uses UDP 67.
Usage in URLs
Sometimes port numbers are clearly visible on the Internet or on other uniform resource locators, such as URLs. HTTP uses TCP port 80 by default and HTTPS uses port 443. Other variations also exist. For example, the URL http://www.example.com:8080/path indicates that the web browser is connecting to 8080 instead of an HTTP server.
List of UDP and TCP ports
As noted earlier, the IANA, or InternetA ssigned Numbers Authority, is responsible for the global coordination of DNS-Root, IP addressing, and other Internet protocol resources. These procedures include registering commonly used ports for known Internet services. All port numbers are divided among themselves into three ranges: well-known, registered and private or dynamic. Known ports are numbers from 0 to 1023. They are also called system ports. The requirements for new values in this range are more stringent than for other registrations.
Examples
Examples of ports that are on the known list include:
- TCP 443 port - HTTPS;
- 21 - File Transfer Protocol;
- 22-Secure Shell;
- 25 - simple mail transfer protocol STMP;
- 53 - DNS domain name system;
- 119 - Network News Transfer Protocol or NNTP;
- 80 – HTTP hypertext transfer protocol;
- 143 - Internet Message Access Protocol;
- 123 - NTP network time protocol;
- 161 is a simple SNMP network management protocol.
Registered ports are required to have numbers from 1024 to 49151. The Internet Assigned Numbers Authority maintains an official list of all known and registered ranges. Frequency or dynamic ports range from 29152 to 65535. One use case for this range is time ports.
History of creation
The concept of port numbers was developed by the early creators of ARPANET. It was developed in an informal collaboration between software authors and system administrators. At that time, the term "port number" was not yet used. The number string of the remote host was a 40-bit number. The first 32 bits resembled today's IPv4 address. The most significant in this case was the first 8 bits. The less significant part of the number (these are bits 33 to 40) denoted an object called AEN. It was a prototype of the modern port number. The creation of a socket number catalog was first proposed on March 26, 1972. Network administrators were then called upon to describe each permanent number for network services and its features. This catalog was subsequently published in RFC 433 in the winter of 1972. It included a list of hosts, their port numbers, and the corresponding function used by each node on the network. For the first time, the official meanings of port numbers were documented in May 1972. At the same time, a special administrative function was proposed to maintain this register. The first list of TCP ports included 256 AEN values. They were divided into the following ranges:
- from 0 to 63 - standard functions of the entire network;
- from 64 to 127 - host-specific functions;
- from 128 to 239 - functions reserved for future use;
- from 240 to 255 - any experimental function.
The term AEN in the early days of the ARPANET was also the socket name that was used with the original connection protocol and the Network Control Program component, or NCP. In this case, NCP was the forerunner of today's Internet protocols, which use TCP/IP ports.
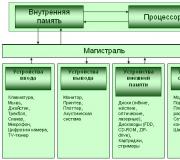
Network ports can provide critical information about applications accessing computers over a network. Knowing the applications that use the network and the corresponding network ports, you can write precise firewall rules and configure host computers to allow only useful traffic through. By building a network profile and deploying tools to detect network traffic, you can more effectively detect intruders - sometimes simply by analyzing the network traffic they generate. We began to consider this topic in the first part of the article published in the previous issue of the journal. It provided basic information about TCP / IP ports as the foundation of network security. Part 2 will describe some methods for networks and hosts that can be used to determine which applications are listening on the network. Later in the article, we will talk about how to evaluate the traffic passing through the network.
Blocking network applications
A network attack surface is a commonly used term to describe a network vulnerability. Many network attacks go through vulnerable applications, and you can significantly reduce the attack surface by reducing the number of active applications on the network. In other words, disable unused services, install a firewall on a dedicated system to validate traffic, and create a comprehensive access control list (ACL) for the firewall at the network perimeter.
Each open network port represents an application listening on the network. The attack surface of every server connected to the network can be reduced by disabling all unnecessary network services and applications. Windows Server 2003 is superior to previous versions of the operating system because fewer network services are enabled by default. However, auditing is still required to detect newly installed applications and configuration changes that open unnecessary network ports.
Every open port is a potential backdoor for hackers who use spaces in the host application or surreptitiously access the application with a different username and password (or use another legitimate authentication method). Either way, an important first step to secure your network is to simply disable unused network applications.
Port scanning
Port scanning is the process of discovering listening applications by actively polling the network ports of a computer or other network device. The ability to read scan results and compare network reports with host port poll results gives you a clear picture of the traffic passing through the network. Knowing the network topology is essential to preparing a strategic plan for scanning specific areas. For example, by scanning a range of external IP addresses, you can collect valuable data about an attacker who has penetrated from the Internet. Therefore, you should scan the network more often and close all unnecessary network ports.
The firewall's external port scan detects all responding services (such as Web or email) hosted on internal servers. These servers should also be protected. Set up a familiar port scanner (for example, Network Mapper - Nmap) to check the desired group of UDP or TCP ports. In general, TCP port scanning is more reliable than UDP scanning due to the deeper feedback it takes from connection-oriented TCP protocols. There are versions of Nmap for both Windows and Unix. Starting a basic scan procedure is simple, although much more complex functions are implemented in the program. To search for open ports on a test computer, I ran the command
Nmap192.168.0.161
Figure 1 shows the results of a scan session - in this case, a Windows 2003 computer in the default configuration. Port scan data shows six open TCP ports.
| Figure 1: A basic Nmap scan session |
- Port 135 is used by the RPC endpoint mapping feature found in many Windows technologies such as COM/DCOM applications, DFS, event logs, file replication, message queuing, and Microsoft Outlook. This port should be blocked in the firewall at the network perimeter, but it's hard to close it and keep Windows functional at the same time.
- Port 139 is used by the NetBIOS session service, which enables the Find Other Computers Browser, File Sharing Services, Net Logon, and Server service. It's hard to close, as is port 135.
- Port 445 is used by Windows for file sharing. To close this port, File and Printer Sharing for Microsoft Networks must be disabled. Closing this port does not prevent the computer from connecting to other remote resources; however, other computers will not be able to connect to this system.
- Ports 1025 and 1026 are opened dynamically and used by other Windows system processes, in particular by various services.
- Port 3389 is used by Remote Desktop, which is not enabled by default, but is enabled on my test machine. To close the port, go to the Remote tab in the System Properties dialog box and clear the Allow users to connect remotely to this computer check box.
Be sure to search for open UDP ports and close the extra ones. The scan program shows open ports on the computer that are visible from the network. Similar results can be obtained using tools located on the host system.
Host scan
In addition to using a network port scanner, open ports on the host system can be detected using the following command (run on the host system):
Netstat -an
This command works on both Windows and UNIX. Netstat lists the active ports on the computer. In Windows 2003 Windows XP, add the -o option to get the corresponding process identifier (PID). Figure 2 shows the Netstat output for the same computer that was previously port-scanned. You should pay attention to the fact that several ports that were previously active are closed.
Firewall log audit
Another useful way to discover network applications that send or receive data over the network is to collect and analyze more data in the firewall log. Deny entries that provide information from the firewall's external interface are unlikely to be useful due to "noise traffic" (eg, worms, scanners, ping tests) cluttering the Internet. But if you log allowed packets from the internal interface, you can see all incoming and outgoing network traffic.
To see "raw" traffic data on the network, you can install a network analyzer that connects to the network and records all detected network packets. The most widely used free network analyzer is Tcpdump for UNIX (the Windows version is called Windump), which is easily installed on a computer. After installing the program, you should configure it to work in the mode of receiving all network packets in order to log all traffic, and then connect it to the port monitor on the network switch and monitor all traffic passing through the network. Configuring the port monitor will be discussed below. Tcpdump is an extremely flexible program that allows you to view network traffic using specialized filters and show only information about IP addresses and ports, or all packets. It is difficult to view network dumps on large networks without the help of appropriate filters, but care must be taken not to lose important data.
Combining Components
So far, we've looked at various methods and tools that can be used to discover applications using the network. It's time to put them together and show you how to determine open network ports. It's amazing how "chatty" computers are on the network! First, it is recommended that you familiarize yourself with the Microsoft document "Service overview and network port requirements for the Windows Server system" ( http://support.microsoft.com/default.aspx?scid=kb;en-us;832017), which lists the protocols (TCP and UDP) and port numbers used by applications and most core Windows Server services. This document describes these services and the associated network ports they use. We recommend that you download and print this helpful reference guide for Windows network administrators.
Setting up the network analyzer
It was noted earlier that one way to determine the ports used by applications is to monitor the traffic between computers using a network analyzer. To see all traffic, you need to connect a network analyzer to a hub or port monitor on the switch. Each port on a hub sees all the traffic of every computer connected to that hub, but hubs are an obsolete technology and most companies are replacing them with switches that provide good performance but are difficult to analyze: each switch port only accepts traffic destined for a single computer connected to to this port. To analyze the entire network, you need to monitor the traffic directed to each switch port.
This requires configuring a port monitor (called span port or mirrored port by different vendors) on the switch. Installing a port monitor on a Cisco Catalyst switch from Cisco Systems is easy. You need to register on the switch and activate the Enable mode, then go to the configure terminal mode and enter the interface number of the switch port to which all controlled traffic should be sent. Finally, all monitored ports must be specified. For example, the following commands monitor three Fast Ethernet ports and forward a copy of the traffic to port 24.
Interface FastEthernet0/24 port monitor FastEthernet0/1 port monitor FastEthernet0/2 port monitor FastEthernet0/3 end
In this example, a network sniffer connected to port 24 will look at all outgoing and incoming traffic from computers connected to the first three ports on the switch. To view the created configuration, enter the command
Write memory
Initial Analysis
Consider an example of analyzing data passing through a network. If a Linux computer is used for network analysis, a comprehensive view of the type and frequency of packets on the network can be obtained using a program such as IPTraf in Statistical mode. Traffic details can be found using the Tcpdump program.
In computer networks, a port is the communication endpoint in the operating system. The term is also used for hardware devices, but in software it is a logical construct that identifies a particular process or service.
A port is always associated with a host IP address and a type, and thus completes the session address assignment. It is identified for each address and protocol by a 16-bit number commonly known as the port number. Specific port numbers are often used to identify specific services. Of the thousands listed, 1024 well-known port numbers are protected by convention to identify specific types of services on a host. Protocols that primarily use ports are for process control (such as Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) of the Internet protocol suite).
Meaning
TCP ports are not needed over direct point-to-point links when the computers at each end can only run one program at a time. They became necessary after machines were able to run more than one program at a time, and were connected to modern packet-switched networks. In the client-server architecture model of the application, ports and network clients are connected to service initiation, provide multiplexing services, after the initial communication is associated with a known port number, and it is released by switching each request service instance to a leased line. A connection is made to a specific number, and thanks to this, additional customers can be served without waiting.
Details
Data transfer protocols - Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) - are used to indicate the destination port number and source in their segment headers. The port number is a 16-bit unsigned integer. So it can range from 0 to 65535.
However, TCP ports cannot use number 0. A source port for UDP is optional, and a value of zero means none.
A process binds its input or output channels over an internet socket (a type of file descriptor) using a transport protocol, a port number, and an IP address. This process is known as bonding, and it enables data to be sent and received over the network.
The operating system is responsible for transmitting outgoing data from all application ports to the network, as well as forwarding incoming network packets (by matching the IP address and number). Only one process can bind to a specific IP address and port combination using the same transport protocol. Common application crashes, sometimes referred to as port conflicts, occur when multiple programs try to communicate with the same port numbers on the same IP address using the same protocol.
How they are used
Applications that implement shared services often use a specially reserved and well-known list of TCP and UDP ports to accept service requests from clients. This process is known as listening, and it involves receiving a request from a well-known port and establishing a one-to-one conversation between the server and client using the same local port number. Other clients may continue to connect - this is possible because a TCP connection is identified as a chain of local and remote addresses and ports. Standard TCP and UDP ports are defined by convention under the control of the Internet Assigned Numbers Authority (IANA).
The core network services (primarily WorldWideWeb) tend to use small port numbers - less than 1024. Many operating systems require special privileges for applications to bind to them because they are often considered critical to the functioning of IP networks. On the other hand, the end client of the connection tends to use a large number of them dedicated for short-term use, so there are so-called ephemeral ports.
Structure
TCP ports are encoded in the header of the transport protocol packet, and they can be easily interpreted not only by the transmitting and receiving computers, but also by other components of the network infrastructure. In particular, firewalls are typically configured to distinguish between packets based on their source or destination port numbers. Redirection is a classic example of this.
The practice of trying to connect to a range of ports in series on the same computer is known as port scanning. This is usually due to either malicious failure attempts or network administrators are looking for possible vulnerabilities to help prevent such attacks.
Actions directed at how often computers are monitored and recorded. This technique uses a number of spare connections in order to ensure an uninterrupted connection to the server.
Examples of using
The most important example where TCP / UDP ports are actively used is the Internet mail system. The server is used to work with e-mail (sending and receiving), and generally needs two services. The first service is used for transport by email and from other servers. This is achieved with the SMTP service application typically listening on TCP port number 25 to process incoming requests. The other service is POP (entirely Post Office Protocol) or IMAP (or Internet Message Access Protocol) which is required for email client applications on users' machines to receive email messages from the server. The POP services are listening on TCP port 110. The above services can both run on the same host machine. When this happens, the port number distinguishes the service requested by the remote device - the user's PC or some other mail server.
While the server's listening port number is well defined (IANA calls them well-known ports), this client setting is often chosen out of the dynamic range. In some cases, clients and the server individually use specific TCP ports assigned by IANA. A good example is DHCP, where the client always uses UDP 68 and the server uses UDP 67.
Application in URLs
Port numbers are sometimes clearly visible on the Internet or other Uniform Resource Locators (URLs). By default, HTTP uses 443 and HTTPS uses 443. However, there are other variations. For example, the URL http://www.example.com:8080/path/ indicates that the web browser is connecting to 8080 instead of the HTTP server.
List of TCP and UDP ports
As noted, the Internet Assigned Numbers Authority (IANA) is responsible for the global coordination of DNS-Root, IP addressing, and other Internet Protocol resources. This includes registering commonly used port numbers for known internet services.
Port numbers are divided into three ranges: well-known, registered, and dynamic or private. Well-known (also known as system) are those with numbers from 0 to 1023. The requirements for new assignments in this range are more stringent than for other registrations.
Well known examples
Examples on this list include:
- TCP 443 port: HTTP Secure (HTTPS).
- 22: Secure Shell (SSH).
- 25: Simple Mail Transfer Protocol (SMTP).
- 53: Domain Name System (DNS).
- 80: Hypertext Transfer Protocol (HTTP).
- 119: Network News Transfer Protocol (NNTP).
- 123: Network Time Protocol (NTP)..
- 143: Internet Message Access Protocol (IMAP)
- 161: Simple Network Management Protocol (SNMP)1.
- 94: Internet Relay Chat (IRC).
Registered ports are numbers from 1024 to 49151. The IANA maintains an official list of known and registered ranges. Dynamic or private - 49152 to 65535. One use case for this range is for ephemeral ports.
History of creation
The concept of a port number was created by the early developers of ARPANET through an informal collaboration between software authors and system administrators.
The term "port number" was not yet in use at the time. The number string for the remote host was a 40-bit number. The first 32 bits were similar to today's IPv4 address, but the first 8 bits were the most significant. The least significant part of the number (bits 33 to 40) denoted another entity, which was called AEN. This is the prototype of the modern port number.
On March 26, 1972, the creation of a catalog of socket numbers was first proposed in RFC 322. They called for each permanent number to be described in terms of its functions and network services. This directory was subsequently published in RFC 433 in December 1972 and included a list of hosts, their port numbers, and the corresponding function used on every node on the network. In May 1972, the official assignments of port numbers, network services were documented for the first time, and a special administrative function was proposed to maintain this registry.
The first list of TCP ports had 256 AEN values, which were divided into the following ranges:
- 0 to 63: standard functions of the entire network
- 64 to 127: host-specific features
- 128 to 239: reserved for future use
- 240 to 255: Any experimental feature.
The Telnet service received its first official assignment of a value of 1. In the early days of the ARPANET, AEN was also a socket name used with the original Connection Protocol (MSP) and Network Control Program (NCP) component. At the same time, NCP was the forerunner of modern Internet protocols using TCP / IP ports.
Hello everyone, today I will tell you how the TCP protocol differs from UDP. The transport layer protocols following IP in the hierarchy are used to transfer data between application processes implemented in network nodes. A data packet received from one computer to another via the Internet must be transferred to the handler process, and precisely for a specific purpose. The transport layer takes responsibility for this. At this level, the two main protocols are TCP and UDP.
What do TCP and UDP mean
TCP– a transport protocol for data transmission in TCP/IP networks, which preliminarily establishes a connection to the network.
UDP– a transport protocol that transmits datagram messages without the need to establish a connection in an IP network.
I remind you that both protocols work at the transport layer of the OSI or TCP / IP model, and understanding how they differ is very important.
Difference between TCP and UDP protocols
The difference between TCP and UDP protocols is the so-called “delivery guarantee”. TCP requires a response from the client to which the data packet is delivered, an acknowledgment of delivery, and for this it needs a pre-established connection. Also, the TCP protocol is considered reliable, while UDP has even received the name “unreliable datagram protocol. TCP eliminates data loss, duplication and mixing of packets, delays. UDP allows all this, and it does not require a connection to work. Processes to which data is sent over UDP must make do with what they receive, even with losses. TCP controls the congestion of the connection, UDP controls nothing but the integrity of received datagrams.
On the other hand, due to such non-selectivity and lack of control, UDP delivers data packets (datagrams) much faster, therefore, for applications that are designed for high bandwidth and fast exchange, UDP can be considered the optimal protocol. These include network and browser games, as well as streaming video viewers and applications for video communication (or voice): from the loss of a packet, complete or partial, nothing changes, it is not necessary to repeat the request, but the download is much faster. The TCP protocol, being more reliable, is successfully used even in mail programs, allowing you to control not only traffic, but also the length of the message and the speed of traffic exchange.
Let's look at the main differences between tcp and udp.
- TCP guarantees the delivery of data packets in unchanged form, sequence and without loss, UDP guarantees nothing.
- TCP enumerates packets during transmission, but UDP does not.
- TCP operates in duplex mode, in one packet you can send information and confirm receipt of the previous packet.
- TCP requires a pre-established connection, UDP does not require a connection, it is just a data stream.
- UDP provides higher data transfer rates.
- TCP is more reliable and controls the communication process.
- UDP is preferable for programs that play streaming video, videophony and telephony, network games.
- UPD does not contain data recovery features
Examples of UDP applications, for example, are transferring DNS zones to Active Directory, where reliability is not required. Very often they like to ask such questions at interviews, so it is very important to know the differences between tcp and udp.
TCP and UDP headers
Let's look at how the headers of the two transport protocols look like, since here the differences are cardinal.
UDP header
- 16 bit source port > Specifying the source port for UDP is optional. If this field is used, the recipient may send a response to this port.
- 16 bit destination port > Destination port number
- 16 bit UDP length > Message length including header and data.
- 16 bit checksum > Header and data checksum to check
TCP header
- 16 bit source port > Source port number
- 16 bit destination port > Destination port number
- 32 bit sequence number > The sequence number is generated by the source and used by the destination to reorder packets to create the original message and send an acknowledgment to the source.
- 32 bit acknowledgment number > If the ACK bit of the Control field is set, this field contains the next expected sequence number.
- 4 bits header length > Information about the beginning of the data packet.
- reserve > Reserved for future use.
- 16 bit checksum > Header and data checksum; it determines if the packet has been corrupted.
- 16 bit urgent pointer > In this field, the target device receives information about the urgent nature of the data.
- Parameters > Optional values that are specified if necessary.
The window size allows you to save traffic, consider when its value is 1, then for each sent response, the sender waits for confirmation, which is not entirely rational.
With a window size of 3, the sender already sends 3 frames, and waits for 4, which implies that he has all three frames, +1.
I hope you now have an idea about the differences between tcp udp protocols.
Sources: Wikipedia, Microsoft, portscan.ru
How to find out what ports are open on a computer?
- For Windows: Start → "cmd" → Run as administrator → "netstat -bn"
- In an antivirus program such as Avast, it is possible to view active ports in the Firewall: Tools -> Firewall -> Network Connections.
Also useful netstat commands:
To display both the Ethernet statistics and the statistics for all protocols, type the following command:
netstat -e -s
To display the statistics for only the TCP and UDP protocols, type the following command:
netstat -s -p tcp udp
To display active TCP connections and the process IDs every 5 seconds, type the following command:
nbtstat -o 5
To display active TCP connections and the process IDs using numerical form, type the following command:
nbtstat -n -o
For TCP sockets, the following status values are valid:
| CLOSED | Closed The socket is not being used. |
| LISTEN (LISTENING) | Waiting for incoming connections. |
| SYN_SENT | Actively trying to establish a connection. |
| SYN_RECEIVED | The initial synchronization of the connection is in progress. |
| ESTABLISHED | Connection established. |
| CLOSE_WAIT | The remote side has disconnected; waiting for the socket to close. |
| FIN_WAIT_1 | The socket is closed; disconnecting the connection. |
| CLOSING | The socket is closed, then the remote side disconnected; Waiting for confirmation. |
| LAST_ACK | The remote side disconnected, then the socket is closed; Waiting for confirmation. |
| FIN_WAIT_2 | The socket is closed; waiting for the remote side to disconnect. |
| TIME_WAIT | The socket is closed, but is waiting for packets still on the network to be processed. |
List of most commonly used ports
| № | Port | Protocol | Description |
|---|---|---|---|
| 1 | 20 | FTP Data | File Transfer Protocol - file transfer protocol. Data port. |
| 2 | 21 | FTP Control | File Transfer Protocol - file transfer protocol. Command port. |
| 3 | 22 | SSH | Secure SHell - "secure shell". Operating system remote control protocol. |
| 4 | 23 | telnet | Terminal NETwork. Protocol for implementing a text interface over a network. |
| 5 | 25 | SMTP | Simple Mail Transfer Protocol is a simple mail transfer protocol. |
| 6 | 42 | WINS | Windows Internet Name Service. A service for mapping NetBIOS computer names to host IP addresses. |
| 7 | 43 | WHOIS | Who is. Protocol for obtaining registration data about owners of domain names and IP addresses. |
| 8 | 53 | DNS | Domain Name System - domain name system. |
| 9 | 67 | DHCP | Dynamic Host Configuration Protocol - dynamic host configuration protocol. Getting dynamic IP. |
| 10 | 69 | TFTP | Trivial File Transfer Protocol is a simple file transfer protocol. |
| 11 | 80 | HTTP/Web | HyperText Transfer Protocol is a hypertext transfer protocol. |
| 12 | 110 | POP3 | Post Office Protocol Version 3 - Protocol for receiving e-mail, version 3. |
| 13 | 115 | SFTP | SSH File Transfer Protocol. Secure data transfer protocol. |
| 14 | 123 | NTP | Network Time Protocol. A protocol for synchronizing the computer's internal clock. |
| 15 | 137 | NetBIOS | Network Basic Input/Output System. A protocol for providing network I/O operations. name service. |
| 16 | 138 | NetBIOS | Network Basic Input/Output System. A protocol for providing network I/O operations. Connection service. |
| 17 | 139 | NetBIOS | Network Basic Input/Output System. A protocol for providing network I/O operations. Session service. |
| 18 | 143 | IMAP | Internet Message Access Protocol. Application layer protocol for accessing email. |
| 19 | 161 | SNMP | Simple Network Management Protocol is a simple network management protocol. Device management. |
| 20 | 179 | BGP | Border Gateway Protocol, border gateway protocol. Dynamic routing protocol. |
| 21 | 443 | HTTPS | HyperText Transfer Protocol Secure is an HTTP protocol that supports encryption. |
| 22 | 445 | SMB | server message block. A protocol for remote access to files, printers, and network resources. |
| 23 | 514 | syslog | system log. A protocol for sending and logging messages about ongoing system events. |
| 24 | 515 | LPD | Line Printer Daemon. Protocol for remote printing on a printer. |
| 25 | 993 | IMAP SSL | IMAP protocol that supports SSL encryption. |
| 26 | 995 | POP3 SSL | POP3 protocol supporting SSL encryption. |
| 27 | 1080 | SOCKS | SOCKet secure. Protocol for obtaining secure anonymous access. |
| 28 | 1194 | openvpn | An open implementation of Virtual Private Network (VPN) technology. |
| 29 | 1433 | MSSQL | Microsoft SQL Server is a database management system. Database access port. |
| 30 | 1702 | L2TP (IPsec) | Protocol for supporting virtual private networks. As well as a set of data protection protocols. |
| 31 | 1723 | PPTP | Tunnel protocol for a secure connection to a point-to-point server. |
| 32 | 3128 | proxy | At the moment, the port is often used by proxy servers. |
| 33 | 3268 | LDAP | Lightweight Directory Access Protocol is a lightweight directory access protocol (directory service). |
| 34 | 3306 | MySQL | Access to MySQL databases. |
| 35 | 3389 | RDP | Remote Desktop Protocol is a remote desktop protocol for Windows. |
| 36 | 5432 | PostgreSQL | Access to PostgreSQL databases. |
| 37 | 5060 | SIP | A protocol for establishing a session and transferring multimedia content. |
| 38 | 5900 | VNC | Virtual Network Computing is a system for remote access to a computer desktop. |
| 39 | 5938 | teamviewer | TeamViewer is a system for providing remote control of a computer and data exchange. |
| 40 | 8080 | HTTP/Web | Alternative port for HTTP protocol. Sometimes used by proxy servers. |
| 41 | 10000 | NDMP | Popular port: Webmin, SIP voice, VPN IPSec over TCP. |
| 42 | 20000 | DNP |