Areas of knowledge of software engineering and software life cycle standards. Great encyclopedia of oil and gas
For help in solving a tricky problem with the operating system or devices, it is better to immediately refer to the computer configuration. It can give responders a clue to the problem, and you will quickly receive a substantive answer instead of asking for the configuration. And such a request will inevitably follow, unless you have turned to the community of telepaths who can determine your configuration with the effort of thought.
It's good if you know your configuration by heart. What if not? Then collecting information about the computer configuration requires a couple of minutes and a minimum of effort. Below I will tell you how to do this using Windows OS or third-party programs that can create a report that can be published on the forum.
System information (msinfo32)
As trivial as it may sound, information about your computer’s hardware configuration can be collected without installing third-party programs. Windows OS includes a utility System Information, which has the ability to export collected data to a text file. You can launch the program from the menu Start — Programs — Standard — Service or from the window Start — Execute(or fields Search in Vista) by entering msinfo32 and pressing OK.
After a few seconds, the program will collect information about the system and its hardware configuration. To export a report, select from the menu File paragraph Export, and then specify the file name and save folder. The report is ready! Because it contains a variety of information, the file is relatively large in size. For publication on the forum, it is better to archive it.
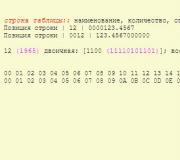
On Windows XP and Vista, the same result can be achieved from the command line by running the command
Msinfo32 /report"<путь к папке>\config.txt"
The report file will be created in the folder whose path you specify in the above command.
Third Party Programs
There are a great many free programs for determining hardware configuration, and it is simply impossible to describe them all. I tested several, paying attention to the following points. The program should be free, small in size and have a clear Russian interface, be able to save the report as a text file or web page, and, if possible, not require installation.
In the end, I settled on two, which won me over with the simplicity of the interface and the minimum of body movements required to create a report.
Winaudit
Along with the hardware configuration, the program collects various information about the operating system and installed applications. You can exclude unimportant information from the report by clicking the button Options and checking the boxes as shown in the image below.

After this you need to press the button again Audit on the report creation toolbar. To save the report, click the button Save, and the program will offer a dozen different formats to choose from. It is better to save the report as a web page (HTML) or text file. When saved as a web page, the program creates three HTML files that can be zipped and attached to a forum post.
System Information for Windows (SIW)
The SIW program is about 2.2 MB in size, does not require installation (although only the English version is offered without an installer), has a well-thought-out interface, and the clarity of the information it displays deserves a very high rating. In the multilingual version, the Russian interface language can be set in the window if necessary Tools -> Options. We are, however, interested in creating a report; this option is in the menu File, as shown in the figure below.
A set of program settings specified by the user.
There are different approaches to storing configuration. Many programs store settings in text files; This is especially typical for UNIX-like systems. On Windows, text configuration files are also used and are often in the .ini format. Despite the fact that in almost all cases these files can be edited manually, in many cases a special interface is created for this (which can be either console or graphical).
Sometimes on UNIX-like systems the configuration is set at the stage of building the program, and to change it the program must be rebuilt. A prime example is the Linux kernel. In almost all applications built on the basis of autoconf, you can enable or disable certain external libraries through parameters to the configure script.
Often a special database is used to store the configuration. Windows uses the Windows Registry, and GNOME uses GConf; in both cases the configuration has a tree structure.
Sources
Write a review about the article "Software Configuration"
Excerpt describing Software Configuration
- Yes, asking for her hand again, being generous, and the like?... Yes, this is very noble, but I am not able to go sur les brisees de monsieur [follow in the footsteps of this gentleman]. “If you want to be my friend, don’t ever talk to me about this... about all this.” Well, goodbye. So you will convey...Pierre left and went to the old prince and princess Marya.
The old man seemed more animated than usual. Princess Marya was the same as always, but because of her sympathy for her brother, Pierre saw in her joy that her brother’s wedding was upset. Looking at them, Pierre realized what contempt and malice they all had against the Rostovs, he realized that it was impossible in their presence to even mention the name of the one who could exchange Prince Andrei for anyone.
At dinner the conversation turned to war, the approach of which was already becoming obvious. Prince Andrei talked and argued incessantly, first with his father, then with Desalles, the Swiss teacher, and seemed more animated than usual, with that animation whose moral reason Pierre knew so well.
That same evening, Pierre went to the Rostovs to fulfill his assignment. Natasha was in bed, the count was at the club, and Pierre, having handed over the letters to Sonya, went to Marya Dmitrievna, who was interested in finding out how Prince Andrei received the news. Ten minutes later Sonya entered Marya Dmitrievna’s room.
Program configuration. The program is developed on the basis of a comprehensive configuration for 1C Enterprise 7.7. Thus, if a standard product is purchased, you must have 1C Enterprise 7.7 Integrated Trade Accounting Calculation. If necessary, the program can be implemented in any other configuration in literally 1-3 days. The configuration can be either developed by 1C or developed by dealers, or developed independently.
In this case, it is necessary to combine the client’s configuration with that supplied by the developers, which can be performed by both the client’s specialist and the 1C dealer, as well as the developers themselves. The program stores intermediate data in registers, so the Operational Accounting component is required. The remaining components are optional.
It is important that the configuration in this case is saved in 1C Enterprise 7.7. It is allowed if it was developed in 1C Enterprise 7.5 and then simply saved in a new format. 8,12,21,22,24
End of work -
This topic belongs to the section:
Enterprise budget management
This is a system that is maintained in the format of budgets by responsibility centers. A budget is an accurate calculation of all the resources of an enterprise to achieve... Why do companies switch to budget management? In conditions of fierce competition, company executives are thinking...
If you need additional material on this topic, or you did not find what you were looking for, we recommend using the search in our database of works:
What will we do with the received material:
If this material was useful to you, you can save it to your page on social networks:
| Tweet |
All topics in this section:
Benefits of Budgeting
Benefits of Budgeting. Budget translated from English is a plan or standard, and not necessarily financial. So, the sales budget, from which, in accordance with marketing
Main types of budgets
Main types of budgets. There are many types of budgets used depending on the structure and size of the organization, distribution of powers, characteristics of activities, etc. To two basics
Budget management system
Budget management system. Throughout the world, financial management is ultimately described in the format of three main reports, which provide a frame of reference for assessing financial performance.
Budget planning
Budget planning. Budgeting is a method of allocating quantified resources to achieve quantified goals. Him also
Cost accounting control
Cost accounting control. In modern economic conditions, the efficiency of an enterprise depends primarily on the quality of business management, the basis of which is the management education system.
The place of budgeting in the financial management system and its implementation in the enterprise
The place of budgeting in the financial management system and its implementation in the enterprise. Comparison of financial management tools Table 1 shows the characteristic features of budgeting,
Description of the software product
Description of the software product. Typically, companies have virtually unrelated software support circuits for individual accounting, commercial, and financial functions and services. Hour
Stages of implementing a system solution
Stages of implementing a system solution. Does the methodology break down the implementation process into 8 stages? Determining the needs of the organization? Description of the system solution? Adapting the system to user needs
Filling constants
Filling the constants. When the configuration is launched for the first time, a dialog box appears for filling in the constants of the Budget Management software product, processing the entry of initial data. Moreover, part
Security Settings
Security settings. The information stored in the program is often confidential, so the developers have provided a flexible security system in advance. It is possible to highlight several
First launch of the program
First launch of the program. If at the end of the program installation it cannot launch 1C Enterprise, this is due to the peculiarities of the 1C installation, so launch it through the Programs menu. 2. After normal
Working with the program
Working with the program. After the program is installed and launched for the first time in exclusive mode, it can be fully used. 2. If the first launch occurs from the computer on which
Demonstration of the program
Demonstration of the program. It is recommended to demonstrate the program through a presentation in MS PowerPoint. If the viewer requires nuances to be shown, then it is possible to simultaneously explain individual aspects
Purchasing the program
Purchasing the program. Only planning module seats are licensed and purchased. That is, you need to buy a program for the number of places that will plan to introduce the document
A program is an ordered sequence of commands. The ultimate goal of any computer program is to control hardware. The software and hardware in a computer work inextricably linked and in continuous interaction. Software composition
a computing system is called software configuration. In a software configuration, there is a relationship between its programs, that is, there is an interprogram interface. The possibility of the existence of such an interface is based on the technical specifications and interaction protocols. In practice, the interprogram interface (interaction) is implemented by distributing software across several interacting levels. These levels are a pyramidal structure. Each subsequent level builds on the software of the previous levels. Software levels are divided into basic, system, service and application.
Base Level - The lowest level of software represents the base software. It provides interaction with the underlying hardware. As a rule, these software are included directly in the basic equipment and are stored in special ROM chips. Programs and data are written into ROM chips at the production stage and can be changed during operation only using special means.
The system level is transitional. Programs operating at this level ensure the interaction of other computer system programs with basic level programs and directly with the hardware, that is, they perform “intermediary” functions. Specific programs that provide interaction with specific devices are called device drivers. They are part of the system level software. Programs responsible for
interaction with the user are called enablers
user interface. The collection of system-level software forms the core of the computer operating system. If a computer is equipped with system-level software, then it is already prepared for the installation of higher-level programs and for the interaction of software with the equipment and with the user. The presence of an operating system kernel is an indispensable condition for a person to be able to practically work with a computer system.
The service level is a service program that provides interaction with programs at the basic and system levels. Utilities (utilities) are designed to automate work on checking, setting up and configuring a computer system.
Classification of utility programs:
File managers (file managers), which perform operations related to maintaining the file structure: copying, moving and renaming files, creating directories (folders), deleting files and directories, searching for files and navigating in the file structure;
Data compression tools (archivers), which are intended for creating archives. Archiving data simplifies its storage and increases the efficiency of using the media (memory device) due to the fact that archive files usually have an increased density of information recording;
Viewer and playback tools designed to view and play documents without loading them into the “parent” application system (development environment);
Diagnostic tools designed to automate hardware and software diagnostic processes;
Control (monitoring) tools designed to monitor the processes occurring in the computing complex;
Installation monitors, designed to ensure that there are no disruptions to the performance of other programs when installing and uninstalling software;
Communication tools (communication programs) designed to establish connections with remote computers. They serve to facilitate the transmission of e-mail messages, forwarding of fax messages and many other operations on computer networks;
Computer security tools are means of passive and active protection of data from damage, unauthorized access, viewing and modification.
The application level is a set of application programs with the help of which specific tasks are performed at the workplace.
Classification of application programs:
Text editors designed for entering and editing text data;
Word processors that provide input, text editing and formatting (design) of documents intended for printing, as well as electronic documents intended for display on the screen;
Graphic editors designed for creating and (or) processing graphic images;
Database management systems (DBMS), designed to create a database structure, provide tools for populating this structure or importing data from tables in other databases, provide the ability to access data, and provide tools for searching and filtering data;
Spreadsheets are complex tools for storing and processing various types of data,
presented in the form of tables;
SLB systems (computer-aided design systems) intended for design and engineering work;
Desktop publishing systems designed to automate the process of layout of printed publications;
Expert systems designed to analyze data contained in knowledge bases and issue recommendations upon user request;
HTML editors (web editors), designed for creating and editing web documents (Internet web pages);
Browsers are software tools designed for viewing electronic documents in HTML format;
Integrated office management systems designed to automate the manager’s workplace (creating, editing and formatting simple documents, centralizing the functions of e-mail, fax and telephone communications, dispatching and monitoring the document flow of the enterprise, coordinating the activities of departments, optimizing administrative and economic activities and supply upon request of operational and reference information);
Accounting systems are specialized systems that combine the functions of text and spreadsheet editors, spreadsheets and database management systems;
Financial analytical systems designed for banking and stock exchange structures;
Geographic information systems (GIS), designed to automate cartographic and geodetic work based on information obtained by topographic or aerospace methods;
Video editing systems designed for digital processing of video materials (editing, creating
video effects, defect removal, sound overlay, titles and subtitles);
Educational, developmental, reference and entertainment systems and programs that represent separate categories of application software and have their own developed internal classification systems.
3.3. Operating systems of personal computers
3.2.1. General information about operating systems
The operating system is a complex of system and utility software. On the one hand, it relies on the basic software of the computer, which is part of its BIO8 system (basic input-output system), on the other hand, it itself is the support for software at higher levels - application and most service applications. Operating system applications are usually called programs designed to work under its control.
The main function of all operating systems is mediation. It consists of providing several types of interface:
Interface between the user and the computer hardware (user interface);
Interface between software and hardware (hardware-software interface);
Interface between different types of software (software interface).
All operating systems are capable of providing both batch and interactive modes of operation with the user.
In batch mode, the operating system automatically executes a given sequence of commands.
In interactive mode, the operating system is in a state of waiting for a user command and, having received it, begins execution, and, having executed it, returns a response and waits for the next command.
Based on the implementation of the user interface, a distinction is made between non-graphical and graphical operating systems.
Non-graphical operating systems implement a command line interface. The main control device in this case is the keyboard. It is these systems that provide an interactive mode of operation.
Graphical operating systems implement a more complex type of interface, in which a mouse or an adequate positioning device is used as a control in addition to the keyboard. Working with a graphical operating system is based on the interaction of active and passive on-screen controls. The active control element is the mouse pointer, a graphical object whose movement on the screen is synchronized with the movement of the mouse. Graphical application controls (on-screen buttons, icons, switches, checkboxes, drop-down lists, menu bars, and many others) serve as passive controls.
All operating systems (their kernels) are loaded into RAM automatically when the computer is turned on.