How to connect to someone else's wi-fi without a password. How to connect a laptop (computer) to the Internet via Wi-Fi? Wi-Fi connection problems
Today everything is developing and changing rapidly. The Internet is no longer a development of the US Department of Defense for the exchange of information in case of war, but a common thing for almost all inhabitants of the Earth. But many still need help connecting it.
Let's consider connecting on Windows 7 and 10.
Step 1. You need to check the drivers.
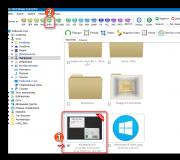
Through start we find “control panel”, open “network and internet”. Select “Network and Sharing Center” and go to “Change adapter settings”. You should see a dual monitor icon that says “wireless network connection.” This is what needs to be turned on. This is the chain of actions for Windows 7.
 There is another way. It is also suitable for Windows 10. Through the start or desktop menu, find and right-click the “my computer” tab or shortcut. Select “properties”. The basic information of your computer will appear before your eyes. On the left, find tabs with yellow and blue shield icons. Among them is the “device manager”. This is what you need. Search for “network adapters” and expand the list. It should have a name containing the word wireless or the numbers 802.11. When selecting it, you must click “enable”.
There is another way. It is also suitable for Windows 10. Through the start or desktop menu, find and right-click the “my computer” tab or shortcut. Select “properties”. The basic information of your computer will appear before your eyes. On the left, find tabs with yellow and blue shield icons. Among them is the “device manager”. This is what you need. Search for “network adapters” and expand the list. It should have a name containing the word wireless or the numbers 802.11. When selecting it, you must click “enable”.
What should you do if the required icon and name are not found? Their absence indicates uninstalled drivers.
Step 2. Installing drivers.
Windows 10 installs the network adapter driver on its own. It can only be updated. Therefore, let's consider this operation using Windows 7 as an example.
So, if you did not find any signs of the existence of a network adapter, you will need to install it yourself.
Method 1. Many people are accustomed to the fact that drivers come on a disk that comes included. However, a disk with them is not always included in the laptop components. But it almost always lies in the box along with the adapters. For example, Tp-Link. If you have such a disk, insert it into the drive and follow the instructions.
Method 2. Still no disk? Don't worry, you can download the driver from the Internet. Are you tormented by the question of what to do because Wi-Fi still doesn’t work? You can do this on your tablet or smartphone with mobile internet. You can visit a neighbor, a friend, or even a café with free Wi-Fi. Remember that you just don’t have Wi-Fi, which means you can connect the cable to a PC or laptop and download it this way. In general, there are enough options, and you can’t help but succeed.
Now to clarify where exactly to download. If you have a desktop PC, then you need to look for the driver on the website of the adapter company. If it’s a laptop, go to the laptop manufacturer’s website. Websites must be official. Enter the model in the search bar, find the “drivers and utilities” section, and then select the OS. Next, look for the “wireless” tab and download the required driver.
Advice: If you see several drivers from different manufacturers, then additionally download a small program called HWVendorDetection and open it. It will tell you which manufacturer you need to choose.
The downloaded driver is most likely zipped, and the installation file in it is in setup.exe format. Launch it and, as in the disk situation, just follow the instructions.
Step 3. Connect Wi-Fi.
There will be a Wi-Fi icon in the lower right corner of the screen. By clicking it, you will see a list of available connections. All you have to do is find yours and connect by entering your password. If you want to connect automatically, just check the box.
Now you can connect Wi-Fi. It doesn't matter if you have a PC or a laptop. But you don’t have to buy an adapter, you can just join your neighbor. It's time to find out how to connect to Wi-Fi without knowing the password.
Getting your neighbor's password by trick (phishing)
 Phishing- This is a way by which you can find out your neighbor's password by deception. For this you will need. This program will make your neighbor connect to another access point, thereby giving you a password.
Phishing- This is a way by which you can find out your neighbor's password by deception. For this you will need. This program will make your neighbor connect to another access point, thereby giving you a password.
This happens as follows:
Step 1. First, the program prepares the hacker’s computer - it does something like tuning the PC:
- configures HTTP and HTTPS;
- searches the wlan0 and wlan1 networks for wireless interfaces until switching to one of them occurs;
- then it goes into monitoring mode and, using DHCP services, displays additional IP addresses;
- displays on the monitor a list of access points available for attack.
Step 2. You need to choose a victim.
After selecting a point, the utility creates a copy of the access point (with the same name) and disables the real one. The victim's Internet starts to drop, and she connects to a pseudo point.
Step 3. Reading information.
You receive connection information via . When a victim tries to open a website, he will be taken to a phishing page, where he will see a network connection error asking for a password. If the password is entered, the Internet will work on the attacked PC, and the program will show this password.
Subsequently, the attacker has access to the router settings, and therefore to network management. He will be able to change the WPS PIN, gain access to information for authorization on various resources, and also redirect visitors to banking sites to fictitious ones.
To protect yourself from such attacks, carefully check sites that ask for a password!
We intercept traffic and decrypt the WiFi password
You can also find out the password through intercepted traffic. For this you will need:
- WiFi Slax;
- Dictionaries for selecting passwords.
Step 2. Security measures
No one has canceled them yet, so we change our mac address:
- open the terminal and enter into it: ifconfig wlan0 down – turn off the adapter;
- open Macchanger: in the interface, select the “other (same)” option and click “change MAC”;
- We return to the terminal and turn on the adapter with the command – ifconfig wlan0 up.
Step 3. Password interception
Launch minidwep-gtk. Let's scan. Let's see what's in the area. We choose a “victim” and attack. It will be thrown out of the network due to interference. Trying to connect to a point, our “victim” will exchange data with it. We will intercept them. This is called a handshake. After receiving it, the program will offer to run a handshake in the dictionary.
Step 4. Decryption
If you downloaded the program from a flash drive, then the algorithm is as follows:
- refuse the program’s offer to search through dictionaries and save to disk;
- open the tmp folder (located in the Home folder) and find 3 handshake files;
- copy them to your hard drive.
You have received your network password in encrypted form. To decrypt, you need a second program - . Install it, select the desired language, and then import the data - the TCPDUMPX file. Next, press Ctrl + I and select the dictionaries that you need to download first. Ready. A simple password will be decrypted in seconds, a more complex password will take more time.
How to connect to Wi-Fi on a laptop
Now you will learn how to connect to your neighbor’s Wi-Fi without knowing the password. There are several ways. But, one way or another, you need to find out the password. You, of course, can visit your neighbor, and when he leaves you alone with the router, look at the combination of numbers on its case. If this option fails, then move on.
Selecting a wi-fi password
You can try to guess the password manually. Many people enter a fairly easy pin like 1234, qwerty or password. Do you know your neighbor's date of birth? Trying is not torture. Didn't it work out? Don't be discouraged. Entrust the matter to a special utility.
Hacking a router and changing the WiFi password
CommView will also act as assistant programs.
Step 1: Installation
The first utility just needs to be unzipped. Before installing the second one, check on the program’s website whether your adapter is supported by it. When you start it for the first time, you will need to patch the drivers and restart the computer, then make the settings:
1. https://yadi.sk/i/JOYKdzXn36vP39
2. https://yadi.sk/i/3HSf3v-p36vP7y
3. https://yadi.sk/i/MTW56bro36vPBb
Step 2: Capture
Click the “capture” button and select “start scanning” in the window that appears. A list of networks will appear. From it you will need to select the one for which you need a password. Click “capture” again and wait for the scan to complete.
Then press the Ctrl and L key combination on your keyboard. Then “file”, “download CommView log files...” and select all the proposed files. Next step: “rules” tab, “export log files” and click “TCPdump format”.
Step 3. Hacking
Now the role of the utility. After opening it, specify the path to the TCPdump format packets. In the settings, select WEP encryption and continue the search using the Launch command. As a result, you will have a window that you can use to log into the network.
Programs for connecting to someone else's Wi-Fi
Decided to connect to your neighbor's Wi-Fi without knowing the password? Your assistants will be:
- Aircrack-ng. A utility that allows you to find and hack wireless networks. Can intercept traffic, WEP audit and encryption keys. It consists of a set of programs, each of which has its own purpose. Also available for iPhone.
. It scans networks for later use. Intercepts signals, disables the victim, analyzes and saves data. Can be used to guess passwords. Breaks WEP and WPA encryption networks.
. This utility is translated as “left connection”. It does not attack https, which are well protected, but intercepts the session ID. You will own the data at a time when the victim does not even suspect anything.
. Useful application based on Android. Do you urgently need Wi-Fi, but there are only buried networks around? Wi-Fi Unlocker will solve your problem. A few clicks and you can use the Internet on your device.
. The utility is designed for traffic analysis and is part of the Aircrack-ng software suite.
 Recently, identification of connected users of the Moscow metro has become a mandatory requirement. These measures are provided to improve the safety of citizens. In order to connect to Wi-Fi in the Moscow metro, you need to perform a few simple steps, namely:
Recently, identification of connected users of the Moscow metro has become a mandatory requirement. These measures are provided to improve the safety of citizens. In order to connect to Wi-Fi in the Moscow metro, you need to perform a few simple steps, namely:
- In the settings of your personal device, select the metro network;
- Open a browser, then type the special address vmetro.ro in the address bar;
- At the time of completing the action, a special window will appear in which you must enter your mobile phone number;
- A special one-time SMS will be sent to your phone; enter it on the website, after which the network connection will become available to you.
Using the government services website. Go through identification. It is carried out through a PC, mobile phone or through an account on the GOST SERVICES website.
In the metro you need to connect to MosMetro_Free, and then go to the vmet.ro website in your browser. Login only in a new window or tab. Next, click “Login to the Internet.” Ready.
The dangers of using someone else's Wi-Fi (or free one)
Open networks are dangerous because anyone can intercept and decrypt traffic, which means they can view information about you and even enter an open session. And if you try hard, you can get to files located on your computer, email, and even e-wallet.
Regarding hacking of someone else's router, an article in the Criminal Code of the Russian Federation provides. Be careful. If you don't want any trouble, buy a router. If you like to take risks, you know where to start.
Contents
- 1 How to connect to a neighbor’s Wi-Fi without knowing the password?
- 1.1 Here are some interesting programs that may solve your problem with the lack of Internet:
- 1.2 Here is a video explaining how the hacking process occurs:
Despite the fact that today connecting to the Internet is not a big problem, many still want to get a connection for free. Wi-Fi is everywhere today, and we could freely surf the Internet anywhere, however, most points are encrypted with a password. But lovers of free things don’t stop there, they are trying to find a way. Well, since the topic is so exciting, I will try to talk about it in detail. Let's start with the fact that Wi-Fi is wireless Internet. The advantage of such a connection is that the user does not have to fuss with wires. You just need to connect a router that will distribute the Internet within a certain radius. A huge number of devices can be connected to the router, so Wi-Fi is a very convenient thing for large families or public places.
As for public places, wireless Internet is usually available to everyone there. It is there precisely for the people, and not for a certain circle of people. In this way, many establishments attract visitors, because today free Wi-Fi really attracts.
If you live near a large shopping center or other similar "establishments", then perhaps you will find a point where there is no password. Also, if there are cafes, restaurants and other similar establishments nearby, then here we can get free Internet. Today, there are more and more Wi-Fi points every day, but most of the points are still password-protected, so for those who like freebies, the growth of Wi-Fi points is not a big advantage.
Who sets the password for wireless Internet in most cases? Either companies in their offices, or ordinary people living in their homes. Few people are generous with the Internet these days, and connection speeds drop when too many people connect to Wi-Fi, so hotspot owners don’t like to distribute the Internet to everyone.
How to connect to a neighbor's Wi-Fi without knowing the password?So, we were unlucky with our neighbors, since they are all “greedy” for the Internet. We went through the list of Wi-Fi points, but they are all “locked”, so you will have to somehow break this lock, or connect your router yourself and forget about this problem (which is what I recommend you do).
They block their Wi-Fi from strangers using an encryption system.
I won’t describe the hacking procedure for you step by step. Those who want to find the appropriate programs will find them (and then the program will do everything for you).
I would like to devote this article, rather, to the options with which it will be possible to find a way to connect to someone else’s wireless Internet. I’ll also tell you how this procedure actually happens.
By the way, the article will be useful not only to those who want to get free Internet, but also to those who want to protect their Wi-Fi. After all, knowing the hacking methods, you will understand how to prevent this hacking.
First, we need to understand whether all operating points near us are indeed “password-protected.”

Now let's imagine that we were unable to connect to any of our neighbors' Wi-Fi because of the password. I personally am against password hacking. And if you are looking for an answer to the question: how to connect to a neighbor's Wi-Fi without knowing the password, accordingly, you want to hack someone else's access point.
Today, a router is quite inexpensive. So it would be better for you to just go to your Internet provider and sign an agreement with them. By giving a small amount of money every month, you will save yourself from unnecessary troubles associated with the Internet. What kind of troubles might arise?
By hacking your neighbor's Internet, you show your attitude towards your neighbor. And if a neighbor finds out that you are using his Internet without permission, trouble may arise. After all, who knows, maybe you don’t have the calmest person living next to you.
I have already mentioned that there are programs for hacking. And I will briefly mention them so that you do not waste a lot of time searching for special utilities.
How does this program actually work? There is a huge database containing a wide variety of programs. We enter the access point to which we want to connect, and using this database the program tries to find the correct Internet password. Naturally, the result of hacking is not 100%, but, as practice shows, the probability of gaining access to “password-protected” Wi-Fi is quite high.
Here are some interesting programs that may solve your problem with the lack of Internet:
- Aircrack-ng

- AirSlax (download the latest version of the program)

- Sidejacking
Despite the fact that the programs are in English, their interface is very simple, so it won’t be difficult to understand.
Any of the presented utilities will try to connect to the specified Internet point by selecting the correct password until it finds the correct password. Therefore, sometimes you can get access to free Internet in 5 minutes, and sometimes in 5 days. After all, no matter how smart the program is, it is not capable of “running through” a million possible passwords in a minute.
Essentially, we don’t need to do anything to attempt a hack. Do you want to know How to connect to a neighbor's Wi-Fi without knowing the password? Install one or all programs at once, specify the access point you want to hack, and the program will do the rest for you. I also want to recommend another program - CommView for Wi-Fi. It does not hack hotspots, but provides detailed information about them and monitors available Wi-Fi hotspots. By the way, such a program will be useful for those who want to know absolutely all the information about THEIR Wi-Fi connection.

In fact, all programs work according to the same “scheme”, so it doesn’t really matter which utility you decide to choose. By the way, if your neighbor’s Internet keeps turning on and off, there’s no point in hacking it, and the program won’t be able to guess the password while the connection is interrupted.
By the way, if you yourself do not want to face such a situation that your point was hacked using the program I mentioned, set a very complex password.
Sometimes even the most powerful program is not able to hack the connection. Therefore, you should not be so sure that using some utility you will quickly gain access to Wi-Fi. If a point has a password made up of a huge number of letters, numbers and symbols, then the probability of hacking is practically zero.
Here's a video explaining how the hacking process works:
I'm not saying that hacking other people's networks is a good way to get free Internet. Remember that your “victim” of hacking may be extremely unhappy with this situation. And if the victim manages to find out that you managed to hack the Internet connection, then you may get into trouble. Firstly, you are breaking the law (but no one will put you in jail because of this), and secondly, the owner of the Wi-Fi point can “punish” you for such an act. I'm just warning you about the possible consequences of hacking.
Unlike company-owned access points, which are typically protected, it is highly likely that your neighbor's home router is not configured correctly.
Unlike company-owned access points, which are typically protected, it is highly likely that your neighbor's home router is not configured correctly. The term "neighborly" is used here in the sense that to successfully hack, you need to be in close proximity to the victim (which is generally not a problem if you have an external antenna). Recently, many utilities have appeared (such as “Wifite”), with the help of which even an attacker without special qualifications can penetrate into a nearby Wi-Fi network. Most likely, among your neighbors there are those who use a poorly configured access point. By the way, in order to penetrate the network, it is not at all necessary to be guided by malicious goals, but simply for the sake of curiosity. In addition, by becoming familiar with hacking methods, you can protect your own Wi-Fi network.
List of utilities used:
Obtaining a password for the access point
The choice of one or another attack method depends on the configuration of the victim’s Wi-Fi network. Each security standard has its own vulnerabilities that can be exploited by an attacker.
Open hotspots
Open access points, although rare, do occur, which indicates either “generosity” towards neighbors or complete ignorance in security matters (or both of these factors). It is believed that users with an unlimited channel are more likely than others to leave their routers unprotected.
Attack pattern: in open Wi-Fi networks, packets are not encrypted, and anyone can intercept all traffic (HTTP, mail, FTP). In our case, we intercept traffic on channel 1 using the ‘Airodump-ng’ utility, and then conduct analysis in Wireshark.
Figure 1: Command to intercept traffic on channel 1 on an unprotected network
As a result of the analysis, we found out that the user was connecting to a bank account.

Figure 2: Analysis of intercepted traffic in Wireshark
However, it is unlikely that the bank's services will work through an unsecured protocol (HTTP, FTP, SMPT, etc.) due to the danger, as in the case above, of using the service through an unsecured Wi-Fi network.
Methods of protection: Never leave an access point “open” or unsecured. Configure your router to use a complex WPA2 key (this is discussed below). If for some reason you want to use an open hotspot, use a browser extension.
IV collisions in WEP
WEP is an outdated security standard that is vulnerable to static attacks due to IV collisions. WEP creates a false sense of security, and after the advent of WPA2, it is difficult to imagine that anyone would want to use outdated algorithms.
Attack pattern: Attack patterns against the WEP protocol have been covered in countless articles. We won't go into detail, but will simply refer you to this page.
Methods of protection: Instead of WEP, use WPA2 or AES.
WPS PIN selection
WPS PIN is an eight-digit number associated with the router. If the WPA password is vulnerable to a dictionary attack, the user can set a complex WPA password and, to avoid having to remember a long passphrase, enable WPS. After sending the correct WPS PIN to the router, information about the settings, including the WPA password, is then sent to the client.
Brute force WPS PIN
The WPS standard was implemented incorrectly: firstly, the last digit of the PIN is a checksum, which means that the effective size of the WPS PIN is only 7 digits. Moreover, the registrar (router) checks the PIN in two parts. This means that the first part, consisting of 4 digits, has 10,000 possible combinations, and the second, consisting of 3 digits, has 1000 combinations. That is, in the worst case, an attacker will need 11,000 attempts to guess the PIN, which is quite a bit. Experimenting with direct search, using the 'reaver' utility, we managed to find the WPS PIN within 6 hours.

Figure 3: WPS PIN brute force process
Methods of protection: update the firmware of your router. The new version should include a lock function after several unsuccessful attempts to enter the PIN (WPS lockout policy). If your router does not have such a function, simply disable WPS.
Other ways to get WPS PIN
If an attacker finds out the PIN of a neighbor's router, the effectiveness of further manipulations increases many times and, most importantly, it does not take much time.
Attack pattern: How can a hacker (or your neighbor) find out the WPS PIN? Usually the PIN is written on the backing of the router, which an attacker can examine during a “friendly” visit. In addition, the access point may remain “open” for some time while the user configures the router or resets the settings to factory settings. In this case, an attacker can quickly connect to the router, go to the settings panel (using standard credentials) and find out the WPS PIN.

Figure 4: Router PIN
Once the attacker has learned the PIN, the WPA password is obtained within a few seconds.
Methods of protection: scrape the PIN from the backing of the router and do not leave the access point “open” for one second. Moreover, in modern routers you can change the WPS PIN in the settings panel (change the PIN periodically).

Figure 5: New PIN generation function
Dictionary attack on WPA Handshake
If you use strong WPA passwords, you don't have to worry about dictionary attacks. However, from time to time, some users make their life easier and use a dictionary word as a password, which leads to a successful WPA 4-way handshake dictionary attack.
Attack pattern: the attacker intercepts the WPA 4-way handshake between the client and the access point. Then, using a dictionary attack, the clear password is extracted from the WPA handshake. More details about these types of attacks can be found on this page.
Methods of protection: use complex passwords with numbers, letters in both cases, special characters, etc. Never use phone numbers, date of birth, or other publicly known information.
Phishing via Wi-Fi
If all previous methods fail, good old social engineering comes into play. In fact, phishing is one of the types of social engineering, when the user is forced through deceptive tricks to reveal the password for the access point.
Attack pattern: Usually phishing attacks are carried out via email, but in the case of Wi-Fi, even the most naive user will be suspicious of a request for a WPA password in an email. To make the attack more effective, attackers usually force the user to connect to a fake access point.
WiFiPhisher is a utility written in phython that helps in implementing the above method. First, the attacker's computer is tuned: setting up HTTP and HTTPS servers, searching for wireless interfaces (wlan0 and wlan1), switching one of these interfaces to monitoring mode and allocating additional IP addresses using DHCP services.

Figure 6: Attacker's system setup process
WiFiPhisher then displays a list of the victim's access points, one of which the attacker chooses to attack.

Figure 7: List of victim access points
After the attacker has selected one of the elements from the list, the utility clones the ESSID and tries to disable the original access point, since the attacker needs to ensure that the victim logs in again to the fake access point. If users cannot be disconnected from the original access point, or the attacker is too far from the victim, the attack will fail because no users will be able to connect to the fake access point.
When the victim connects to the fake access point, the attacker is informed that the client has been allocated an IP address. In the picture below we can see that an Android device has connected to the fake access point.
Figure 8: Victim connected to an attacker-controlled access point
After the victim connects to the fake access point and tries to access the web page, the attacker's HTTP or HTTPS server will display a phishing page. For example, if an Android client makes a request to the site www.google.com, the following page will appear instead of the search bar:

Figure 9: One of the phishing page options
The attacker is notified that the victim attempted to access the website and was redirected to a fake page.

Figure 10: Request Notification
The moment of truth comes: either the victim suspects something is wrong and breaks the connection, or enters the WPA password. After entering the password, the victim will be redirected to another page.

Figure 11: Page to which the victim is redirected after entering the password
The password entered by the victim will be displayed in the attacker's console:

Figure 12: Password entered by the victim
Typically, a user enters a password for one of the following reasons:
1. The user assumes that they are connecting to a legitimate access point.
2. The phishing page is very similar to the page issued by the victim’s router.
3. The user wants to connect to an open access point with the same ESSID.
Methods of protection: carefully double-check all pages where you need to enter a password. Never enter your WPA password on suspicious pages.
Once the attacker has obtained the password to the access point, the next destination is the router’s settings panel.
Standard accounts: many users do not change standard accounts to access router settings, which can be easily found on the Internet. Access to the router settings gives the attacker even more privileges when managing the network.
Receiving PIN and other passwords: After gaining access to the settings panel, the attacker rewrites the WPS PIN and other hidden passwords for further use. Retrieving passwords hidden behind asterisks is as easy as shelling pears. For example, to get the passwords for the 'admin' and 'user' accounts, you can use the 'Inspect element' function in the Chrome browser.

Figure 13: Retrieving passwords hidden behind asterisks using the ‘Inspect element’ function
Expanding the sphere of influence: After gaining access to the local network, the attacker begins to collect information about clients, services, ports, etc. This allows the hacker to find potentially vulnerable systems located in the same network segment.

Figure 14: Search for vulnerabilities on other clients on the network
DNS manipulation: In the router settings panel, an attacker can easily change the DNS settings so that clients using banking services are redirected to fake pages.
Consolidation in the system: After gaining initial access, the attacker will certainly want to gain a foothold in your system, even if you have changed your password or other security settings. One way to gain a foothold in the system is to save the WPS PIN (see Figure 5). A more advanced hacker will install a Trojan into the router’s firmware, which will allow access to the Wi-Fi network using the master password. This scheme is implemented as follows. The open source DD-WRT firmware, suitable for many models, adds a Trojan or master password, after which the firmware is updated through the router's settings panel.

Figure 15: Firmware update in settings panel
Conclusion
The purpose of this article is not to encourage you to hack your neighbor’s Wi-Fi network, but to tell you about the most common vulnerabilities in Wi-Fi settings that can be used by an attacker to penetrate your network.
There is a common belief : “Since I have an unlimited channel, I don’t really care about someone gaining access to my system.”.
In some cases, such generosity is worthy of attention, but often your “fat” channel is not the main target of an attacker. A notable case was when someone tried to set up his neighbors after hacking a WEP key and using the neighbor's network to access child pornographic sites. Since access is provided through your network, the police will come to you during the investigation and it is not a fact that you will prove your innocence. Router manufacturers have designed the settings panels to be as convenient as possible. Use security features to the maximum to protect yourself from intrusion from neighbors.
2. Nikita Borisov, Ian Goldberg, and David Wagner. isaac.cs.berkeley.edu. .
Currently, Wi-Fi is one of the most common methods of distributing the Internet in a limited space. Of course, not every point is in the public domain. This picture is most often observed in public places, such as a shopping center or cafe.
But in the residential sector, quite often the points are “classified”. And the more complex the measures to protect them are, the more sophisticated hacking methods appear. Let's look at the most common of them:

Connecting to Wi-Fi from a phone running the Android operating system
If you want to connect to a Wi-Fi network from a mobile device/tablet, you can do this quite simply: by using a hacker similar to those used on a computer. We invite you to try one of the most well-proven applications for cracking Wi-Fi passwords - Wi-FiUnlocker. This program has several advantages:
- a simple and accessible interface that will be quite understandable even to a person who is very far from modern technology;
- powerful reception, which means the ability to connect to any point distributing wi-fi at a distance of up to 1 km;
- economical battery consumption.

To connect to a secure network using Wi-fiUnlocker, you need to follow a few simple steps.
Step one. Download the application to your phone/tablet and turn it on. Click the Hack Wi-fi key button. After this, the Wi-Fi module will automatically load on the device.
Step two. Select a secure network. The program will scan the available sector and show all networks.
Advice. Choose the one that has the strongest signal. Most likely, it is the one closest to you.
Step three. We crack the password. The program begins to select the wi-fi key: scans it, finds all the weak points in the systems, and then the password. You will have to wait a while while the program runs. Then we enter the proposed combination and use the Internet.
As you can see, connecting to Wi-Fi without knowing the password is a very real and not very difficult task. The main thing is patience and attention. We wish you good luck!
How to hack wi-fi password: video
The Internet has become such an integral part of the lives of most that we no longer notice it - as if it had always been there and people did the same things as easily all the time as they do today. However, this is not true and connecting to the network even today requires certain equipment, passwords, payments and tariff plans.
Finding ourselves in an unfamiliar place, we often need urgent access to the network, but how to connect to WiFi without knowing the password? It remains a mystery to many, but connecting to Wi-Fi without a password is possible!
Methods for connecting to a wifi network
There are several ways to connect to Wi-Fi without a password. The most important ones are brute-force attacks, phishing, and key interception.
First of all, try to choose the right combination. At first glance it may seem that this is impossible, but it is not. Often, in order not to forget, people make it as simple as possible. For example, 12345678 or something like that. Imagine yourself in the shoes of someone who sets a simple password to connect to Wi-Fi.
If you couldn’t find the wifi key and you don’t connect, try installing the WifiCrack program. They do not charge money for downloading and using it, but you must remember that this operation is illegal and you do this only in exceptional cases and after making sure that the owner of the Wi-Fi network to which you are planning to connect is not a bank, police or other special structures.
So, now we will find out how to connect Wi-Fi without a password:

How to connect to Wi-Fi without a password if this method did not work? Connecting to someone else's wifi can be a difficult task and may require traffic interception. The optimal program that can cope with this task is Airslax. It works according to the following principle: when you try to connect to someone else’s network from your phone or from your personal computer, your device still communicates with the router on that side. Packets are being transferred without you even noticing it. And these same data packets contain an encrypted access code. It turns out that if you decrypt these packets, you can get the password. To carry out interception, you need more than average knowledge, but there is nothing overly complicated in this program.
So, let's see how to connect to Wi-Fi without knowing the password using the interception method:

Therefore, we will use the Wifiphisher program to carry out this attack.
- After installing the program, the first thing to do is turn off their wireless point. How to do this is at your discretion, but don’t go overboard.
- Then the wifi router will switch to the “Access Point” mode and the program will be able to copy the Name and title of the Access Point.
- The DHCP server will automatically configure itself to this access point and provide our client with a fake page disguised as anything.
- The client will be taken to this page and will likely enter their access point name and password.
- The program will give you an access code and you can connect.
Once again, we want to repeat that no one will be able to identify you or punish you in any way for any of the above actions, but, if possible, it is always better to ask the owner of the wifi network for the password.